Introducing Encrypted Client Hello (ECH)
It’s been a while since the last update from the TunnelBear anti-censorship team! While there are a lot of exciting changes that we’re not quite ready to share just yet, one thing we are happy to announce is that TunnelBear officially supports Encrypted Client Hello (ECH) for our Android app.
ECH is an important technology to support, and we wanted to take the time to share this accomplishment and discuss the challenges and impact of helping users maintain access to a more open and secure internet.
First, it's important to understand what exactly ECH is.
What is ECH?
Encrypted Client Hello (ECH) is the latest technology available that helps keep the connection to our backend infrastructure private from third parties (ISPs, governments, hackers, etc.) that might otherwise intercept or observe your network connection.
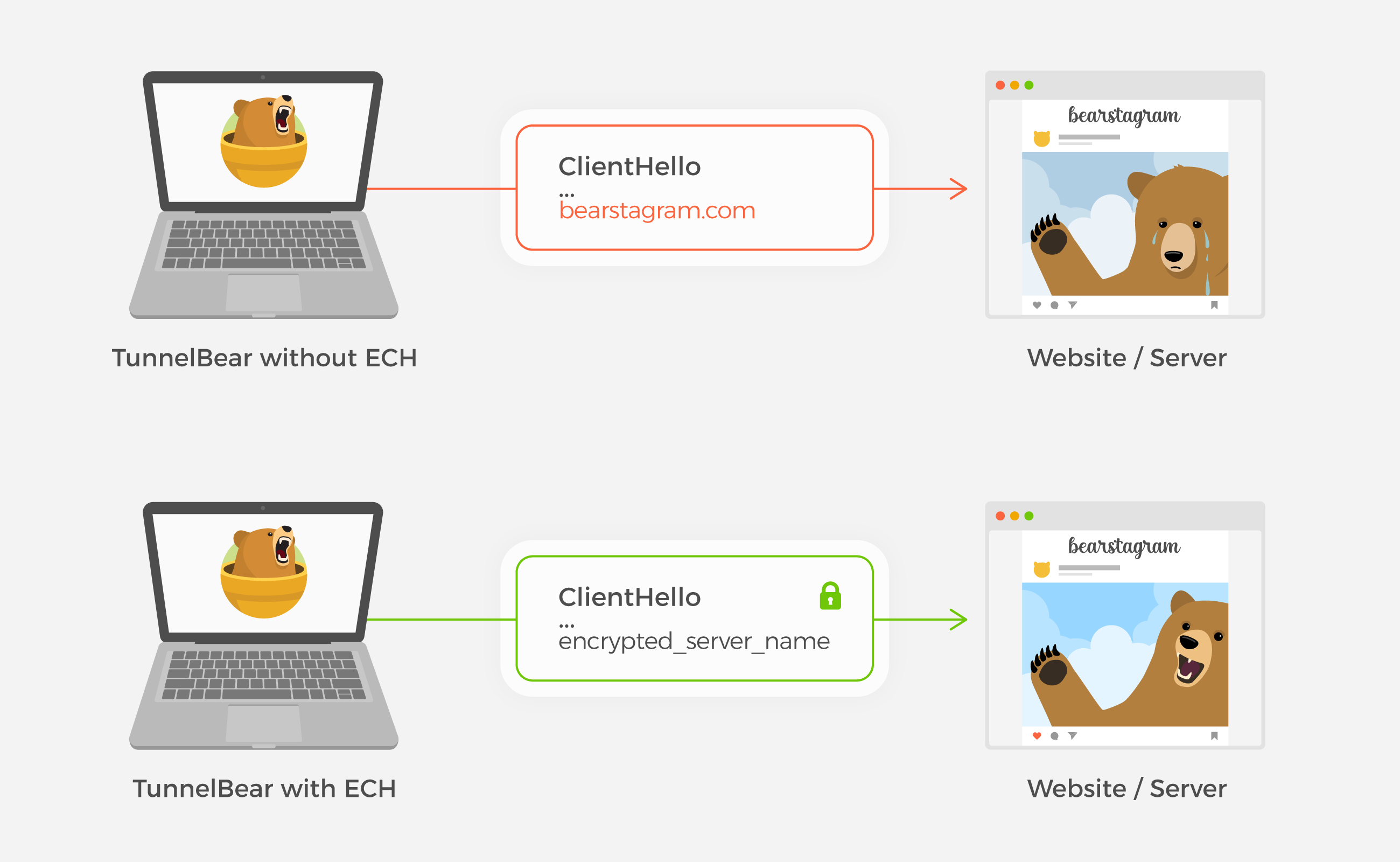
ECH is an extension of the TLS protocol. It aims to secure the TLS handshake portion of the protocol by encrypting the name of the websites you visit, which was previously in plain-text.
A TLS handshake is important to protect because it provides a secure/encrypted connection between the TunnelBear app and our backend servers. These servers are important because they help manage your account and authenticate your connection to the VPN.
The importance of ECH
Not only is supporting the latest anti-censorship technologies important in securing user connections, but ECH also helps reduce existing TLS handshake shortcomings.
While we do support other TLS extensions such as ESNI (Encrypted Server Name Indicator), this technology was the community's first attempt in closing some of the gaps on the SSL/TLS protocol, and there are some limitations as a result.
Unfortunately, the internet was not designed with privacy in mind.
So what does all of this mean? Though TunnelBear helps keep your browsing traffic private, it's still possible for censors to fingerprint and block that traffic if they detect that a VPN is being used. ECH can help make this more difficult for them to achieve.
By combining many different tools and supporting more technologies, we can further reduce the rate at which users are blocked from connecting to TunnelBear and accessing an open internet.
Development efforts
Since ECH is still in it's infancy, documentation and dev support are sparse. We've had to do a lot of testing against Cloudflare's implementation to try and verify our results. Furthermore, essential libraries used for the TLS protocol do not support ECH, meaning we had to modify this ourselves.
While this did make for a more difficult development cycle, we were able to push through these challenges by breaking development into 2 crucial parts; making an ECH request, and gauging its effectiveness.
Making an ECH request:
- To make an ECH request we used a fork of OpenSSL developed by the DEfO project (Developing ECH for OpenSSL).
- We integrated this into our Android networking library (OkHttp) by modifying Google’s Conscrypt and BoringSSL libraries.
- Once this was done, we leveraged Cloudflare’s TLS terminating server by creating the ability to parse its DNS record for its ECH configurations and pass it to our modified libraries.
With this, we were able to send requests to our backend with the SNI encrypted!
Gauging its effectiveness:
- We validated the SNI encryption by inspecting the network traffic as well as using Cloudflare’s trace API.
- To verify the impact of our ECH solution, we implemented a test where we make 3 types of requests: a standard request, a request with our existing anti-censorship technologies, and a request with ECH.
- Each request has a special identifier to differentiate the technology used and allows us to compare them against each other for effectiveness.
This step provided us with insight into how often ECH was used in countries known for censorship, and how successful the connection attempts were.
Helping users access a more open internet
Unfortunately, ECH by itself isn't a perfect solution for users experiencing censorship. As such, it's important that we support as many anti-censorship technologies as possible.
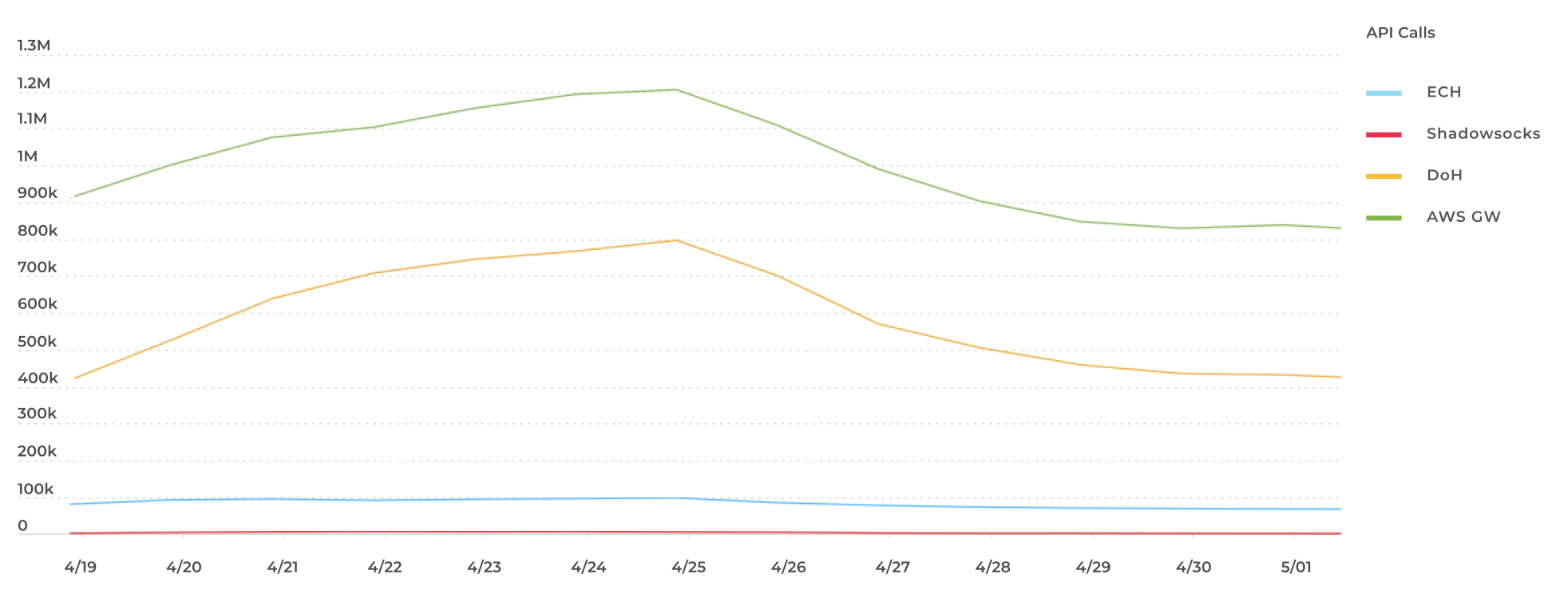
Since adding support for ECH to our Android client, we have achieved approximately 100,000 daily requests that are successfully made to our backend (using ECH). These requests allow users to log in to their accounts, update credentials, obtain their VPN bandwidth, and more.
We have found that in countries where ECH is enabled for users, it increases the likelihood that these API requests are successfully made by approximately 20%. That said, not every user requires ECH in order to use TunnelBear, and there are some countries that are more successful at blocking this technology.
Given the number of successful backend API calls being made, our support has demonstrated that ECH enabled requests have been very effective at bypassing some censorship techniques for many TunnelBear users.
The future of ECH adoption
For ECH to be truly effective as a technology, it needs to be more widely adopted. The more people or services that utilize ECH, the more successful it will be at defeating censorship and building a democratic internet for all.
If you want to help speed up it’s adoption, you can try enabling ECH for your browser (though word of caution, browser support is experimental at this time):
- Firefox: Instructions for enabling ECH on Firefox can be found here
- Enterabout:config
- Searchnetwork.dns.echconfig.enabledand set to true
- Searchnetwork.dns.use_https_rr_as_altsvcand set to true - Edge: Instructions for enabling ECH on Edge can be found here
- Right-click the Edge desktop icon
- Select Properties > Target
- Update the Target to:edge.exe --enable-features=EncryptedClientHello - Chrome: Not supported at this time, currently in development
Our own ECH support is by no means complete. We plan on making further improvements to our Android app, Windows support is currently in the works, and we will begin efforts to support ECH for our macOS and iOS apps in the near future.
We're committed to continue working with censorship researchers worldwide, and we can’t wait to share our next team update soon!
Sincerely rawrs,

