How to Secure Your Customers’ Data Over Insecure Public Wi-Fi
4 minute read
Due to the widespread availability of free public Wi-Fi, more and more remote employees are splitting their time between home and remote workspaces like cafés and hotels. However, while the average person loves public Wi-Fi for its convenience, few know about its security risks.
In a survey of 500 CIO and senior IT decision-makers, iPass found that 81% of respondents had seen Wi-Fi related security incidents in the previous 12 months and that most of those incidents were believed to occur at cafés, airports, and hotels.
. . . help keep your employees safe, no matter where they connect . . .
You can help keep your employees safe, no matter where they connect, by educating them about the risks of using unsecured Wi-Fi. To make that easy, here's a detailed breakdown of the three most significant–and common–attacks that could impact remote workers.
Public Wi-Fi Risk #1: Unsecured / poorly secured networks
Difficulty to identify: Low
Unlike networks that feature the now-standard WPA2 security protocol, your teams' connection to insecure/poorly secured networks is—unsurprisingly—not secure. Because there's no encryption between the router and your teammate's device, attackers can use free tools to "sniff" the data they send to and from their device. The worst part is how common risky Wi-Fi networks are.
According to a recent study from Wandera, Wi-Fi routers with poor to no security manage nearly 70% of all Wi-Fi sessions. The same study found that at least one employee used unsecured Wi-Fi a month at over half of the companies surveyed.
While one employee might not sound like much, if that person were to handle sensitive customer data over an insecure network, an attacker could gain unauthorized access to confidential customer information.
Public Wi-Fi Risk #2: Rogue networks
Difficulty to identify: Medium
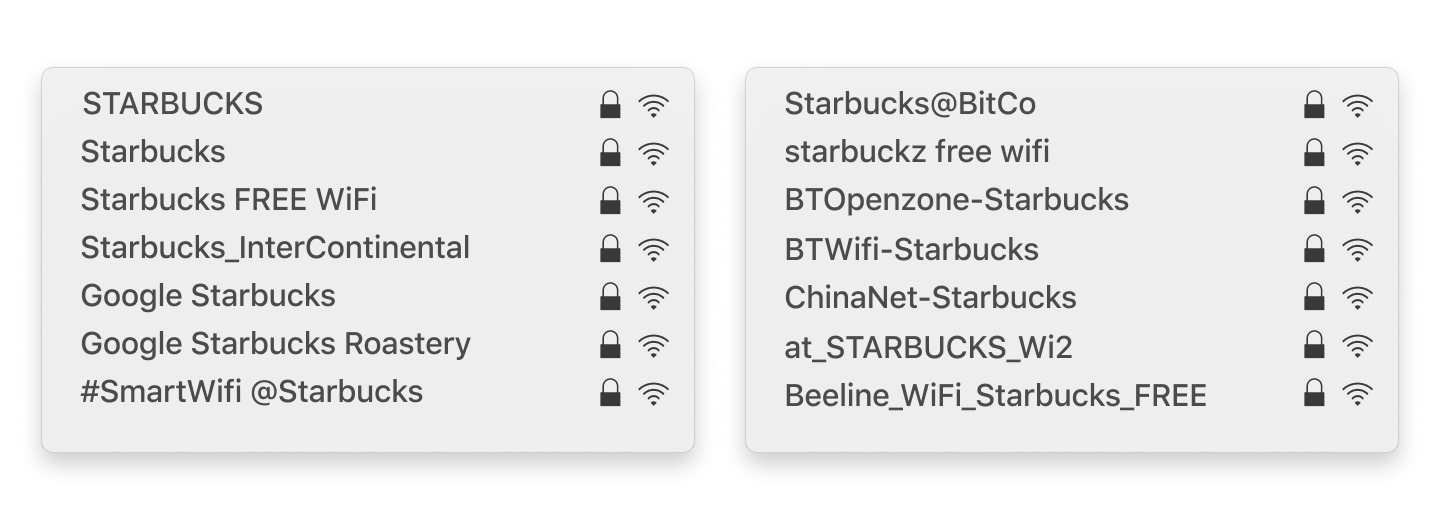
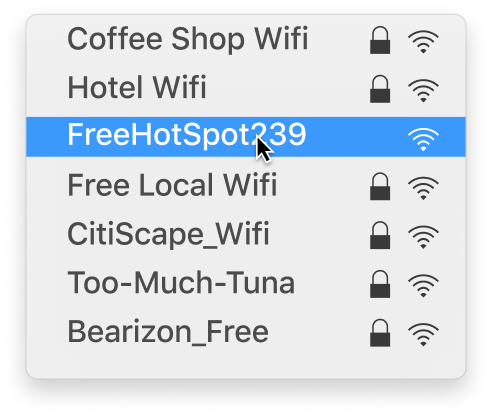
Many public Wi-Fi network names, also known as SSIDs, are comprised of the business name they're owned by and the words FREE and Wi-Fi. Given this well-known naming convention, attackers with cheap, consumer-grade equipment can deploy a similarly-named network in the area—using the same password and even stronger signal strength than the original.
. . . devices will always prioritize the strongest signal available, an attacker's fake hotspot will often be the first on their list.
Because your teams' devices will always prioritize the strongest signal available, an attacker's fake hotspot will often be the first on their list. The image below features a list of rogue Wi-Fi hotspot names that iPass discovered. If one of these were at the top of your available networks list, would you think twice before connecting?
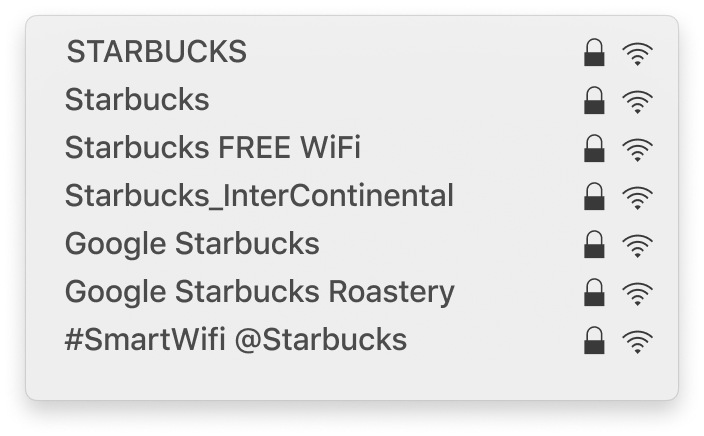 "Starbucks is such a frequently visited location for mobile users that hackers are attempting to capture this huge audience by disguising their rogue hotspots as legitimate Starbucks networks." - Wandera
"Starbucks is such a frequently visited location for mobile users that hackers are attempting to capture this huge audience by disguising their rogue hotspots as legitimate Starbucks networks." - Wandera
Connecting to rogue networks leaves your team vulnerable to having their browsing recorded or traffic rerouted to phishing sites designed to steal login credentials.
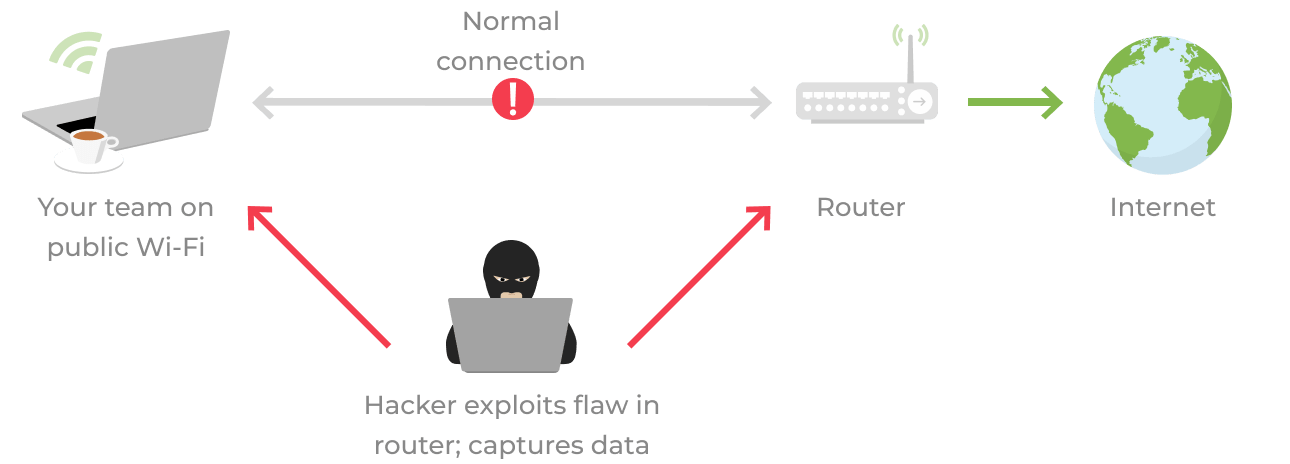
Public Wi-Fi Risk #3: ARP Spoofing
Difficulty to identify: Hard
ARP spoofing is similar to a rogue network, but instead of tricking your team, ARP spoofing tricks their devices into connecting to an attacker's network. If your employee's connection is compromised, an attacker can run man-in-the-middle attacks to log their activity, or even reroute their traffic to start a password phishing scheme.
To ensure they don't arouse suspicion, an attacker can record all of the target's data before sending it on to its intended destination, making it appear as though your team is browsing the web safely. Just like previous attacks, ARP spoofing isn't hard. Basic knowledge of networking and freely available software are all someone needs to attack a network this way.
The easiest solution is the least realistic
Unfortunately, the most popular way that business owner's prevent public Wi-Fi security issues is by banning their usage altogether, but according to Verizon, employees regularly ignore Wi-Fi bans. They found that 81% of office workers polled admitted to using public Wi-Fi, even though their office had a strict ban!
Employees need flexible work options, and if they feel pressured to finish their work outside of the office, or outside office hours, they're going to find a way to do it. Helping them stay secure on those networks is a much more realistic approach.
How to get TunnelBear for Teams
TunnelBear for Teams is an easy and affordable way to protect your entire team with secure Wi-Fi anywhere they need to stay productive. Not only does it secure against all of the attack vectors above, but it also gives team owners a simple way to manage user accounts and billing.
For just $69 per user, a year, squeezing a few extra hours of productivity makes security more than worth the cost. Not to mention the need to keep sensitive customer data safe.
Learn more about TunnelBear for Teams at tunnelbear.com/teams.