Phishing Scams Have Evolved and This is how They Steal Billions
One of software's primary goals has been to make tasks easier to perform. SaaS (Software as a Service) businesses have made everything from editing pictures to keeping in touch with family easier for “non-technical” people. What happens when the altruism that fuels innovation is embraced by enterprising criminals, though? You end up with Phishing as a Service, or PaaS.
Phishing as a Service businesses create software that allow anyone to run an effective phishing campaign, with little to no understanding of how the technology works. What’s more, they’ve streamlined the process by creating email templates that are more effective at tricking people into clicking through.
Gone (mostly) are the days of Princes trying to reclaim lost fortunes or winning random foreign lotteries. Today’s phishing emails look like the same old annoying transactional emails you get from FedEx, Google and other legitimate companies. To protect yourself, you’re going to have to learn about how Phishing has evolved.
Optimizing for conversion
Marketers know that removing distractions from a web page makes it easier for people to buy products. Too much text or confusing buttons are examples of things that could stop someone from tapping "Buy Now". Using marketing best practices, Phishing as a Service developers have optimized their software to make it easier for people to quickly type in their personal information, before they realize something is wrong.
Tracking how emails perform is another core part of email marketing that PaaS developers have included. Comprehensive dashboards give Phishers the ability to see how many people open their emails based on different subject lines, or how many people click through to webpages they've created that steal logins. Something as simple as changing a few words in an email can have drastic effects on how people perceive their email. For phishing emails to work, they have to accomplish two things:
- They have to look like they’re coming from a trusted source
- They have to disguise the action they want people to perform
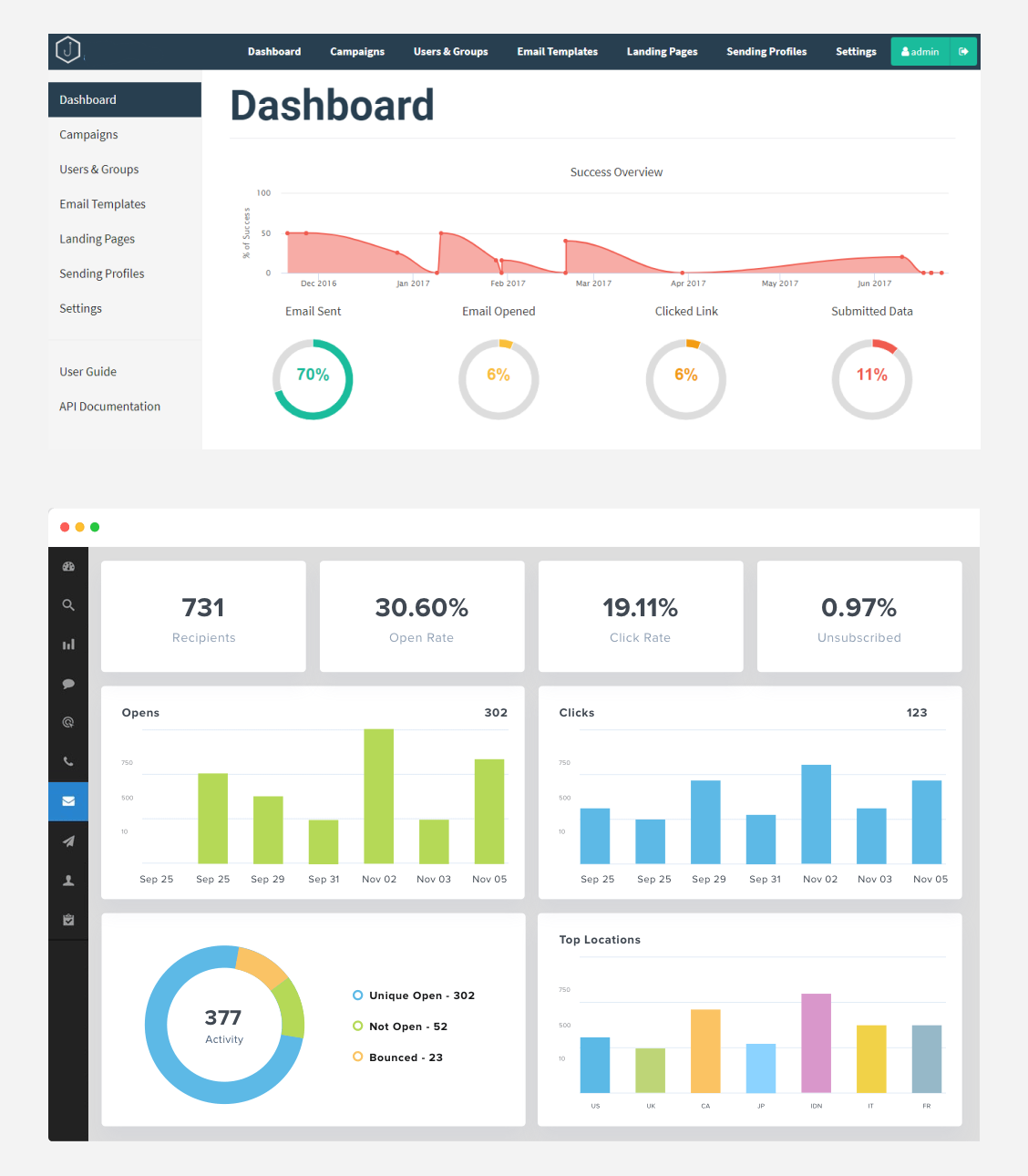
Which dashboard is for marketing?
Fake websites on-demand
Another feature of PaaS products is providing website templates that look like legitimate login pages for popular services. It’s not difficult to make a landing page that looks like the login for Office 365, but unless you know how to mask that fake page, the URL and every link on that page are obviously fake.
To make it harder for people to spot phishing emails, PaaS products create nearly perfect recreations of popular companies for on-demand use. PaaS customers can create randomly generated links to use in their phishing emails that look nearly identical to links from the legitimate company. The image below shows a few of the sites that one PaaS provider offered customers.

Premade website templates spoof popular services
How to spot a phishing email
The more sophisticated phishing emails get, the harder they are to spot. Poor spelling, bad grammar and terribly photoshopped logos don’t appear as often as they used to. A large number of phishing emails could easily pass for real communications, but there are always clues that expose them for fake.
Phishing emails will almost always link directly to a page with a login and password field designed to steal your personal information. It's worth mentioning that more and more legit companies are using an authentication technology called "magic links" to verify accounts. Slack, for instance, sends magic links to authenticate new members to a workspace. The great thing about magic links, is that they don't ask for personal information. You just click the link, and you have access.
Always be careful if you get an email telling you to log into one of your accounts. Open a separate tab and go to the site on your own. Search for the address or type it in from memory, but don’t use a link from an email to take you there.
I accidentally clicked the link, what do I do now?
Don't panic. There's an easy way to check if the site you're on is the real thing. Click the little lock in your address bar, like in the image below.
Check the lock
After you've clicked the lock, a small popup screen should appear. From there, click on the “Certificate” section. This is the site's security certificate and it tells you whether or not your connection to the site is secure. It doubles as a safety check because if the certificate is real, it should be filled with the company's real information.
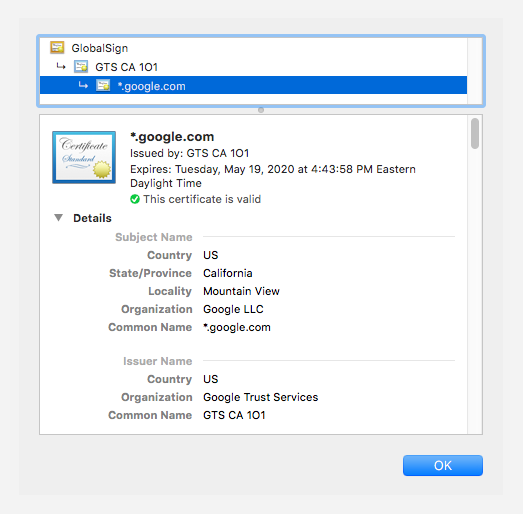
Make sure the certificate is filled out properly
If the information in the certificate window doesn’t match the name of the company you’re trying to reach, or there are multiple blank spaces, do not use it to log into your account. Anyone could have made that website.
What to look for in a phishing email
Whether or not you shop online, you've probably received an email like the one below. This is an email telling you that there are great things happening and if you don't act now, you might miss out on great deals. Seems pretty boring as far as emails go, right?
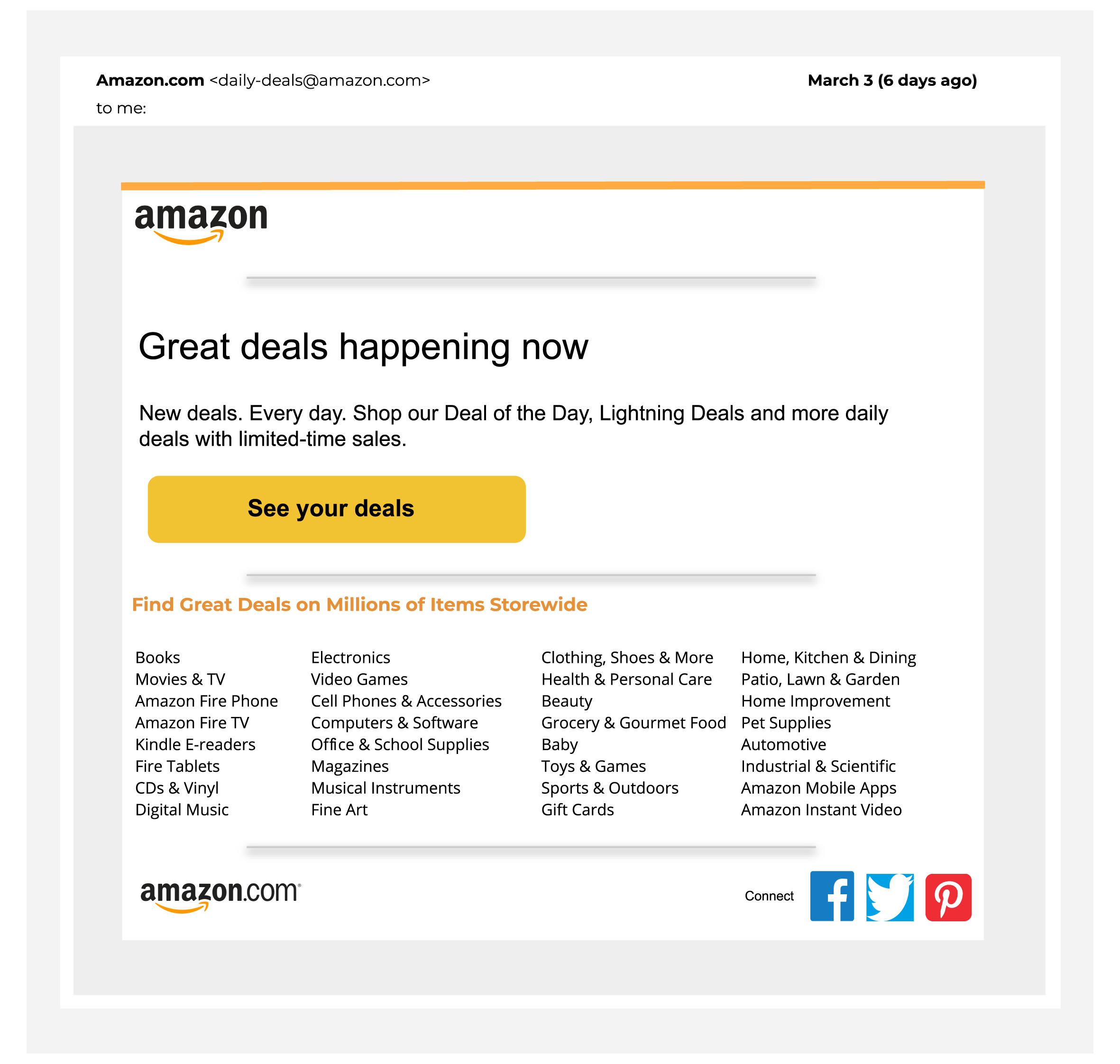
Let's take a closer look.
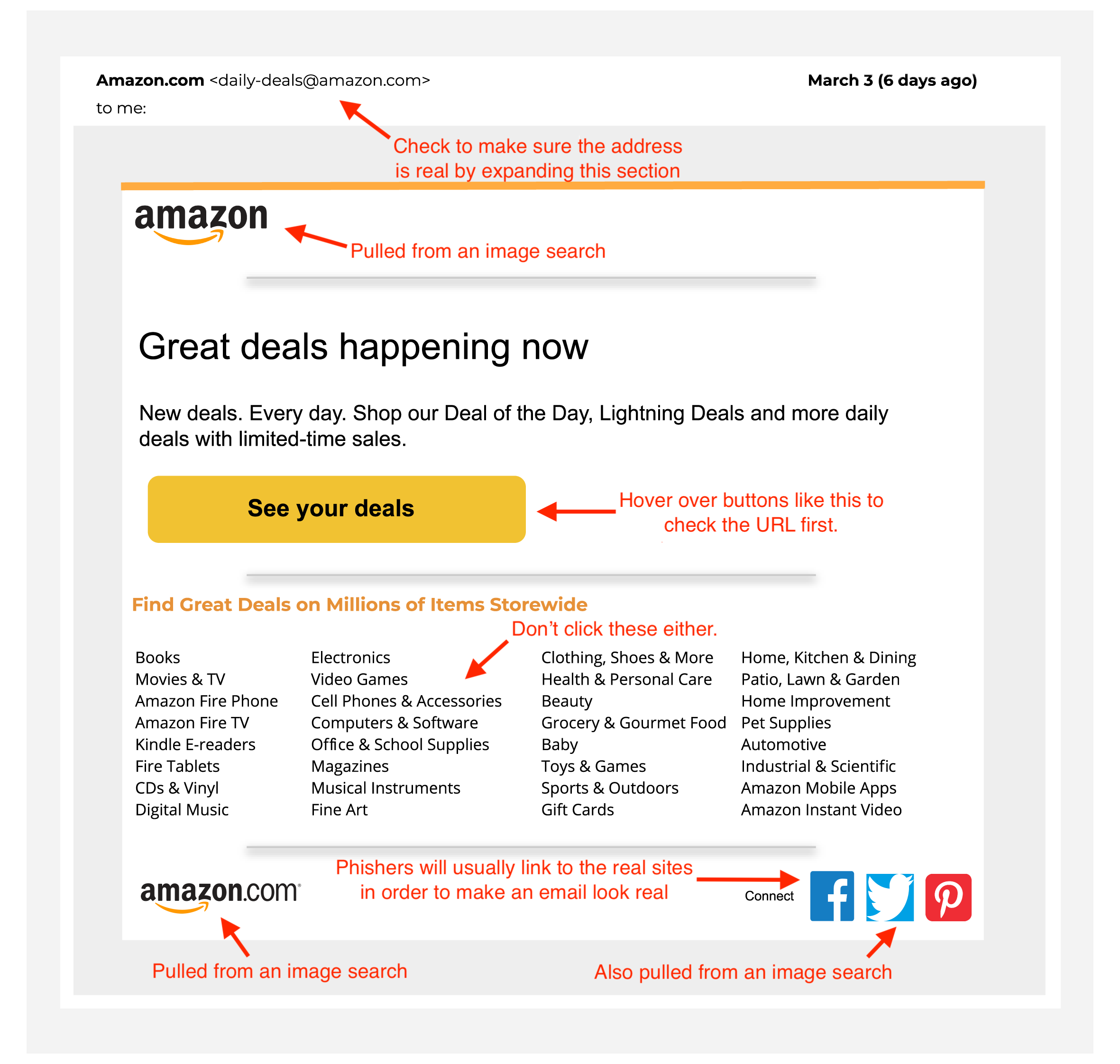
Hopefully, you noticed that things in the first example didn't look right. That's because I made that email with images I found online and Google Slides. It took all of 20 minutes to make something that is very similar to the real thing. For most people, that's all it takes. Something very similar.
The arrows highlight all the things you should look out for. The sender's address looks real, but if you expand the dropdown, you'll likely find an address that is missing a letter, has an odd character in it, or might even be someone's personal email address.
More professional phishing emails will incorporate the business name in the sender email in a believable way, like @[business_name]customersupport.com or customer_service@[business_name].net. They'll most likely have a logo from the company they're impersonating, and might even use the brand colours.
Be sure to hover over any links and see where they actually lead to. The "See your deals" button looks compelling, but chances are it leads to a page asking you to sign in, which you don't want to do. Logos might help make the email look real, but high-res versions of company logos are all over the internet. Don't think that just because the logo is right, the email is safe.
Whether or not an email looks like it really came from a business, don't click through it. Open a new tab and type the URL of the website yourself. If you get an email about an account breach, or a password reset, you can find out if it’s true by visiting the site on your own and trying to login. If there's no indication on your account that someone tried to break into it, you might want to update your password, just in case.
The best way to avoid phishing scams
One of the best ways to avoid phishing emails is to not open unsolicited messages. Even that can be hard though. Some emails you shouldn't ignore, like “forgot password” emails. If you haven't tried to renew a password, but you get an email asking to reset one, it could be a scam or someone trying to log into your account. Either way, you shouldn't ignore that. To protect yourself, you can go to the site directly (through another tab) and check to make sure you can still login. It would be a good idea to change your password, too.
Other emails are more obvious. If you receive an email telling you that you’ve just received a huge tax refund, but you haven’t filed your taxes yet, it's a scam. Don’t have a Dell computer, but you keep getting Dell Support emails? Yup. Scam. You get the point.
Online security takes constant effort
Just like in the real world, you need to be careful about where you go, what you do and who you communicate with online. Be careful when you receive an email from anyone, whether you know the sender or not, because all it takes is one friend of yours to have their email account hacked or a company’s contact lists falling into the wrong hands, and you’re a prime candidate for phishing attacks.
The right tool for the right job
Using the right tool for the right security job is an important part of staying safe online. While TunnelBear doesn't protect you against phishing attacks, it does protect your privacy from your ISP and advertisers. You can learn more about how TunnelBear helps protect you by reading our “What is a VPN” page and by reading more on our blog.
TunnelBear’s free trial gives you 500MB to try out the service and make sure TunnelBear is right for you. We recommend keeping your TunnelBear on all the time, and unlimited subscriptions start as low as just $4.99 a month.
Happy tunneling,


