VigilantBear: Quietly Protecting You From Data Leaks Since 2014
Finding a stable connection to the internet, when you're not at home, isn't always easy. Like most online services, VPN connections can be interrupted without warning. Many providers drop your traffic in the clear during interruptions, giving you the choice of either manually turning off your device’s internet connection, to stop unencrypted data being sent, or to continue browsing unencrypted.
TunnelBear gives you a third option by stopping your traffic automatically if you disconnect. Most people call this a kill switch, but we’ve never really liked the term because it sounds like a switch you activate manually in an emergency. However, we believe the idea behind the feature is important because we want to protect you from sending unencrypted data if your connection to TunnelBear is interrupted.
Today we’d like to reintroduce you to VigilantBear, our answer to unexpected disconnects. After you turn VigilantBear on in TunnelBear settings, it starts protecting you. This feature has been keeping you safe from data leaks for just over three years now, but we still receive a lot of questions about how it works. First, let’s take a look at how we stop unencrypted data from being sent.
Protecting you when your connection is interrupted
Unless you’ve kept a close eye on your device, you could easily keep browsing Facebook or send emails without knowing your VPN has unexpectedly turned off. Interruptions can happen for a number of reasons like your router kicking you off the network briefly or your laptop going to sleep when you close it. If you don’t have a way to stop incoming and outgoing traffic, you could be sending unencrypted private information without even knowing.
We created VigilantBear as a simple, no setup required way to protect you from leaking unencrypted data
One of the ways devices block traffic is with something called a firewall. Firewalls allow traffic in and out of a network through a series of endpoints called ports. A set of rules tells the firewall to open or close ports based on the kinds of traffic you want to allow, and when you want to allow or block them.
We believe blocking all incoming and outgoing traffic is the only way to make sure none of your private information gets sent over the internet unencrypted. If you still have access to the internet while your VPN is down, that means your encrypted tunnel has sprung a leak, metaphorically. Your real IP address could be logged when you visit websites. Your browsing habits could be linked to your device history and any geo-restricted websites could block you now that they know you’re in a different country.
We created VigilantBear as a simple, no setup required way to protect you from leaking unencrypted data, but it’s changed and become smarter over the years.
VigilantBear through the years
When we released the first version for macOS in 2014, it was designed to only block HTTP traffic, the most common form of internet traffic that is not encrypted and highly susceptible to eavesdropping. If an interruption happened, and VigilantBear detected HTTP requests, it redirected traffic to a website that said, “For your privacy we are redirecting your http traffic until your TunnelBear has securely reconnected” until your connection came back. The Windows version was released at the same time and worked in a similar way, but blocked HTTPS traffic requests as well.
It wasn’t the most sophisticated solution, but it did the job. The downside of blocking traffic this way was that some non-HTTP traffic could get through without being encrypted. At the same time, apps that didn’t conform to proxy settings could bypass the HTTP proxy block. It was a good start, but we knew we could do better.
Updates and improvements in version 2 - 2015
Our second release for macOS kept the original HTTP proxy but added firewall rules that allowed HTTPS and DNS traffic so TunnelBear could reconnect, but blocked everything else. It also gave us the ability to block ports to stop background services and other apps from sending unencrypted data while you reconnected to TunnelBear.
For version 2 on Windows, we replaced the proxy altogether and added new rules that blocked all applications, except TunnelBear, while connecting. Once connected, only HTTP and HTTPS traffic were allowed for other applications.
We also released a version for Android in August, 2016, that functions in a very similar way as our macOS version, minus the in-browser warning that VigilantBear is protecting you.
OSX release of version 3.5 - 2017
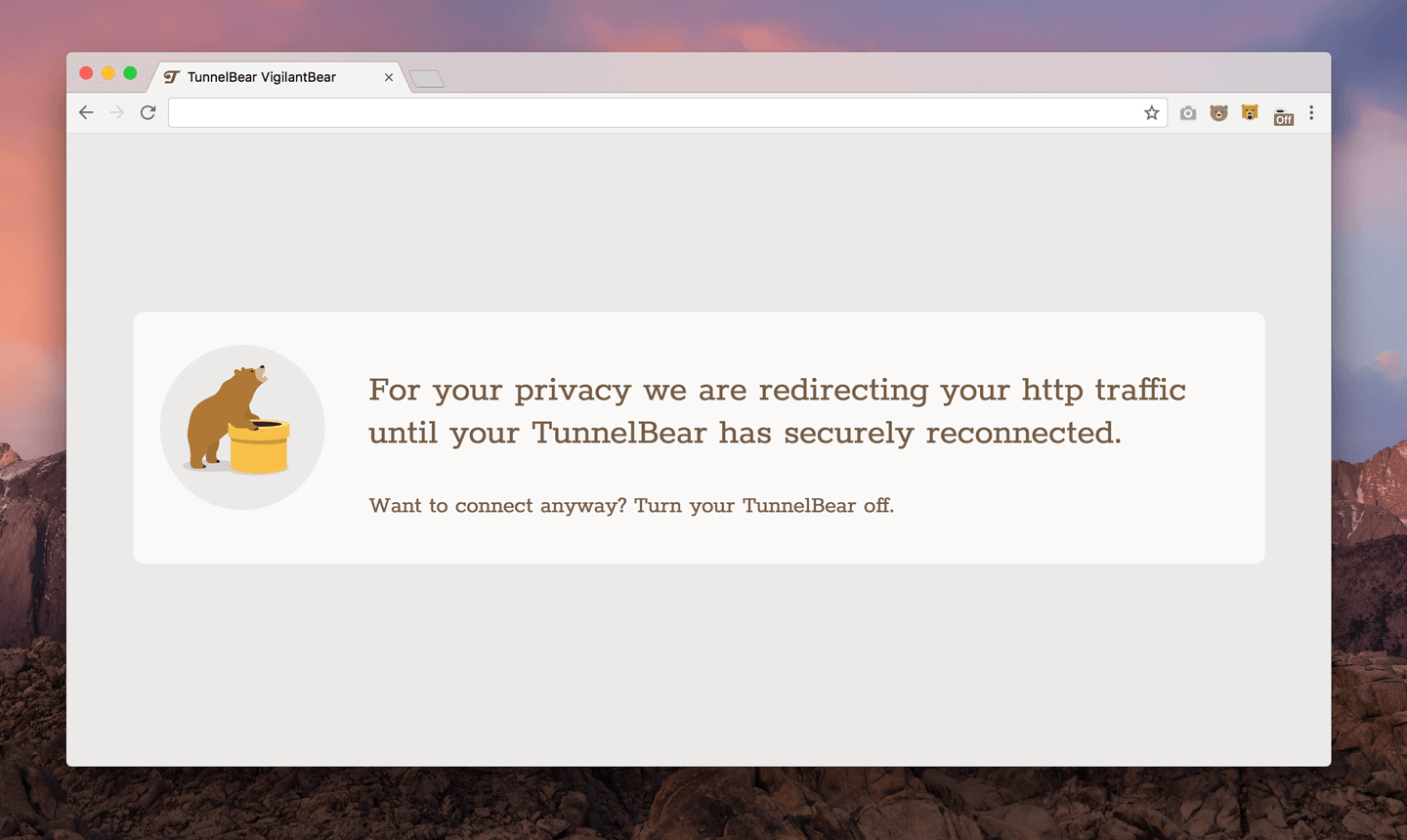
VigilantBear in-browser warning for macOS, 2017
Only ports that are absolutely needed to connect to TunnelBear have access to the internet when re-connecting
Version 3.5 for macOS adds IKEv2 support, for faster connections, and all HTTPS traffic that isn't strictly necesarry for TunnelBear to connect is now blocked by the firewall as well. This means only ports that are absolutely needed to connect to TunnelBear have access to the internet when re-connecting now, so background services and apps are all blocked till the connection made.
Lean and mean
VigilantBear is lightweight, won’t slow down your browsing and is available for macOS, Windows and Android. A note on use though, any services that require an active connection could experience an interruption if you lose your TunnelBear connection.
If you haven’t already enabled the feature, on Mac, you can find it in Settings, Preferences, Security. On Windows, click the gear icon, then the Security tab and tick the VigilantBear option from there. And you can find it on Android by hitting the three lines in the top left hand corner, then Options and selecting VigilantBear in the list.
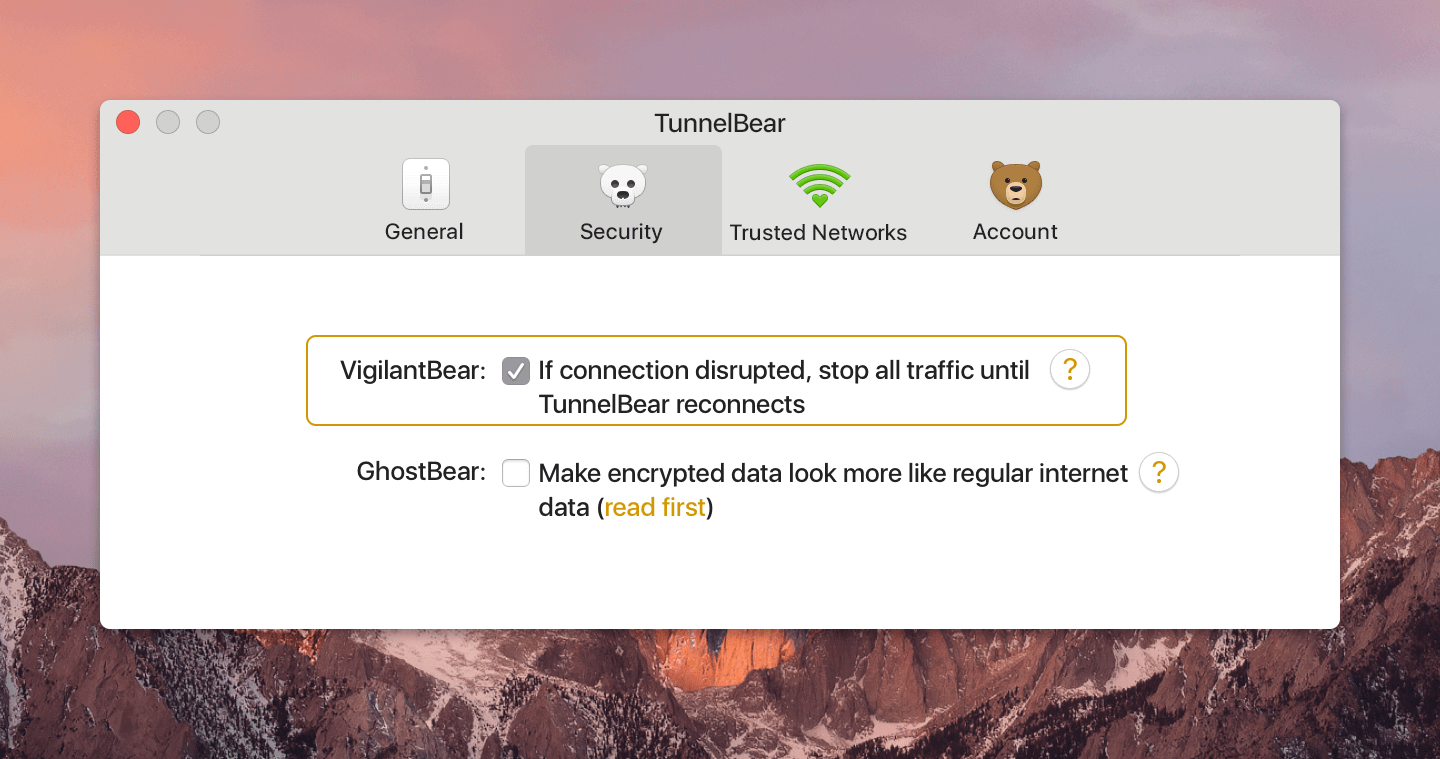
Ever Vigilant
We’ve always encouraged keeping TunnelBear on whenever you browse, and reports have shown that even properly setup security settings for Wi-Fi can be defeated. For reasons like this, we created VigilantBear as another layer of protection to help keep every bit of traffic you send or receive encrypted. Remember that VigilantBear only protects you when you’re in a tunnel and your connection is interrupted, not if the app is open but not connected to TunnelBear.
If you’d like more information about VigilantBear, or you have other questions, you can find most answers on our help page.
Happy tunneling,


