TunnelBear implements OpenVPN3 with Pluggable Transports
Last summer, we discussed new ways the TunnelBear team is helping the internet freedom community’s fight against online censorship, like Encrypted SNI, which allows us to tackle a privacy loophole within HTTPS.
Today, we’re announcing our latest breakthrough: OpenVPN3 with Pluggable Transports. This update tackles the third stage of censorship, by making connections to a VPN more reliable. By advancing obfuscation technology and making it easier for Pluggable Transports to work seamlessly with OpenVPN, TunnelBear is better able to ensure that our users can connect to a VPN server without censor interference.
We’ve open sourced our work so others in the internet freedom space can benefit from our implementation.
In this article we’ll walk you through the implementation and what it means for evading censorship. But first, a bit of background on key concepts -
What is obfuscation?
When your VPN is on, censors can’t see where you’re browsing. However, sophisticated censors may be able to fingerprint and block traffic when it’s sent over the network. If they’re successful, they can block connections from happening in the first place.
This means that even for traffic using strong encryption, it’s important to add another obstacle for censors. This is where obfuscation comes in. Obfuscation (eg. Obs4proxy) is the process of making network traffic harder to understand in order to prevent attack. In a similar way that encryption scrambles information to make it hard to read, obfuscation scrambles the fingerprint encrypted traffic leaves behind making it harder to recognize VPN traffic.
Okay, so what are Pluggable Transports?
Obfuscation techniques need to evolve and be adopted rapidly as censors grow more advanced.
Pluggable Transports provide a way for software developers to rapidly develop and deploy new anti-censorship technologies, a sort of library for them to live in our software. This means that to easily implement new and innovative obfuscation methods, we need to support the Pluggable Transport API in TunnelBear - and by extension, in OpenVPN.
Directly Integrating Obfuscation with OpenVPN
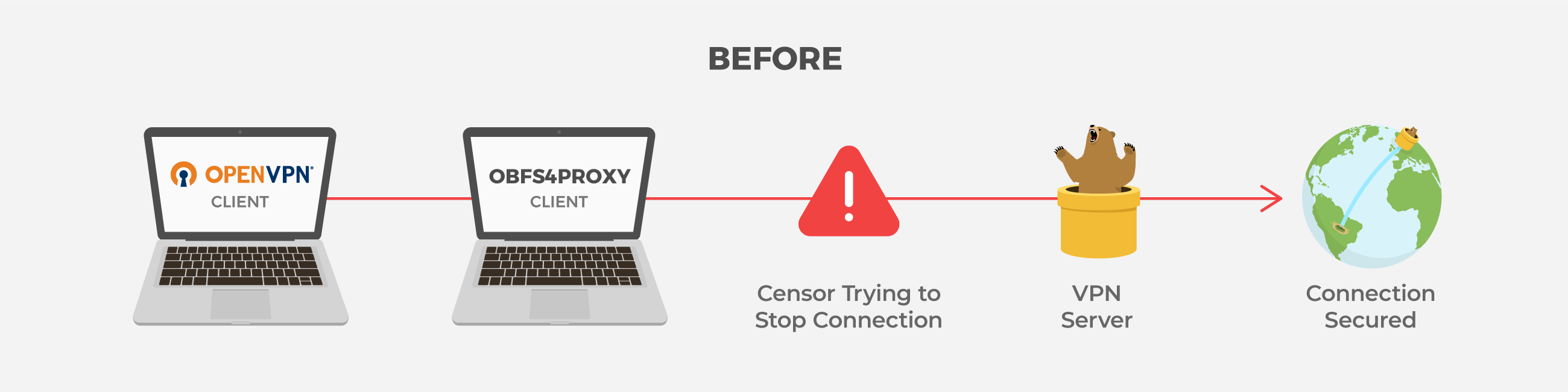
In the previous version of TunnelBear Android, we had OpenVPN2 and Obfs4proxy running as separate processes. This is because OpenVPN2 had no standard way to include obfuscation technology directly, so we had to route the OpenVPN traffic through a second Obfs4proxy tunnel. It’s worth noting, managing both OpenVPN2 and Obfs4proxy is a time consuming and complicated process (that just happens to be forbidden in Android 10).
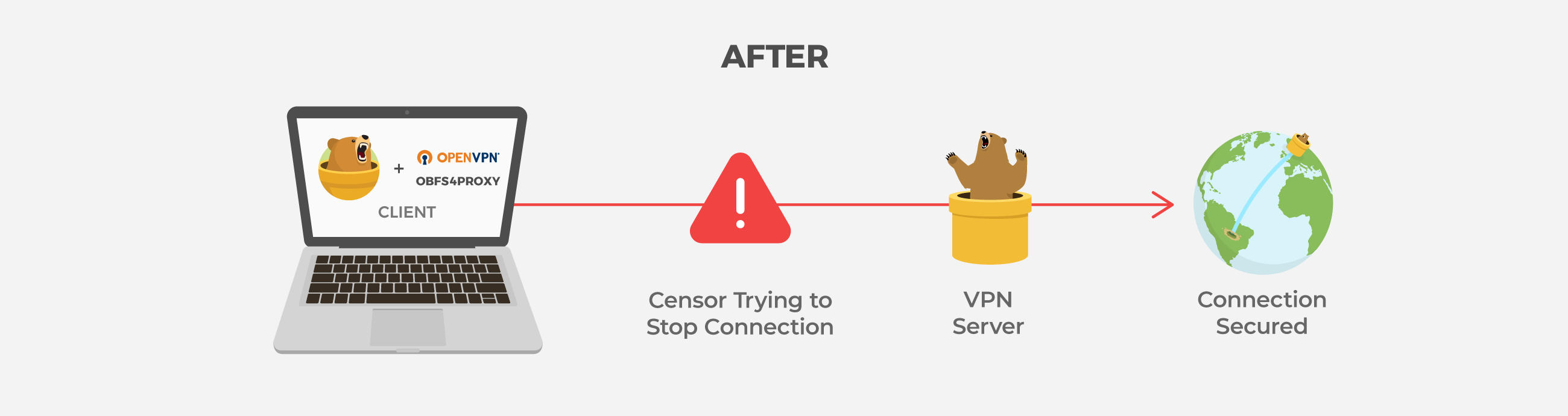
To fix this, we looked for a library version of OpenVPN and Obfs4. Using a library means that we no longer have to run the VPN and obfuscation connections as separate processes, and we can integrate them directly into TunnelBear itself.
We just needed two things: an implementation of Obs4 that can be used as a library, as well as a version of OpenVPN that we could integrate directly into TunnelBear which supports a Pluggable Transports API.
For Obfs4 we relied on the incredible contributions of Operator Foundation, and their shapeshifter-transports project. Operator Foundation have done a lot of work with OpenVPN and Pluggable Transports already - including adding support for Pluggable Transports into OpenVPN2. We created a wrapper that lets us use their code with modern versions of OpenVPN that fit our needs, perfectly.
The benefits of OpenVPN3
Unlike the standard OpenVPN, which requires developers to run it as a separate process, OpenVPN3 is meant to be used by developers as a library, one which can integrate OpenVPN directly into a client app - exactly what we need.
OpenVPN3 had one flaw, it didn’t support Pluggable Transports directly. Luckily, we had a plan.
Over the past few months, we’ve worked on adding Pluggable Transports support to OpenVPN3. We now fully support Obfs4, as well as newer obfuscation technologies, in TunnelBear as needed. Additionally, switching to OpenVPN3 allowed us to support Android 10. There’s an in-depth explanation of our work in thepull request to OpenVPN3.
Where does this leave us?
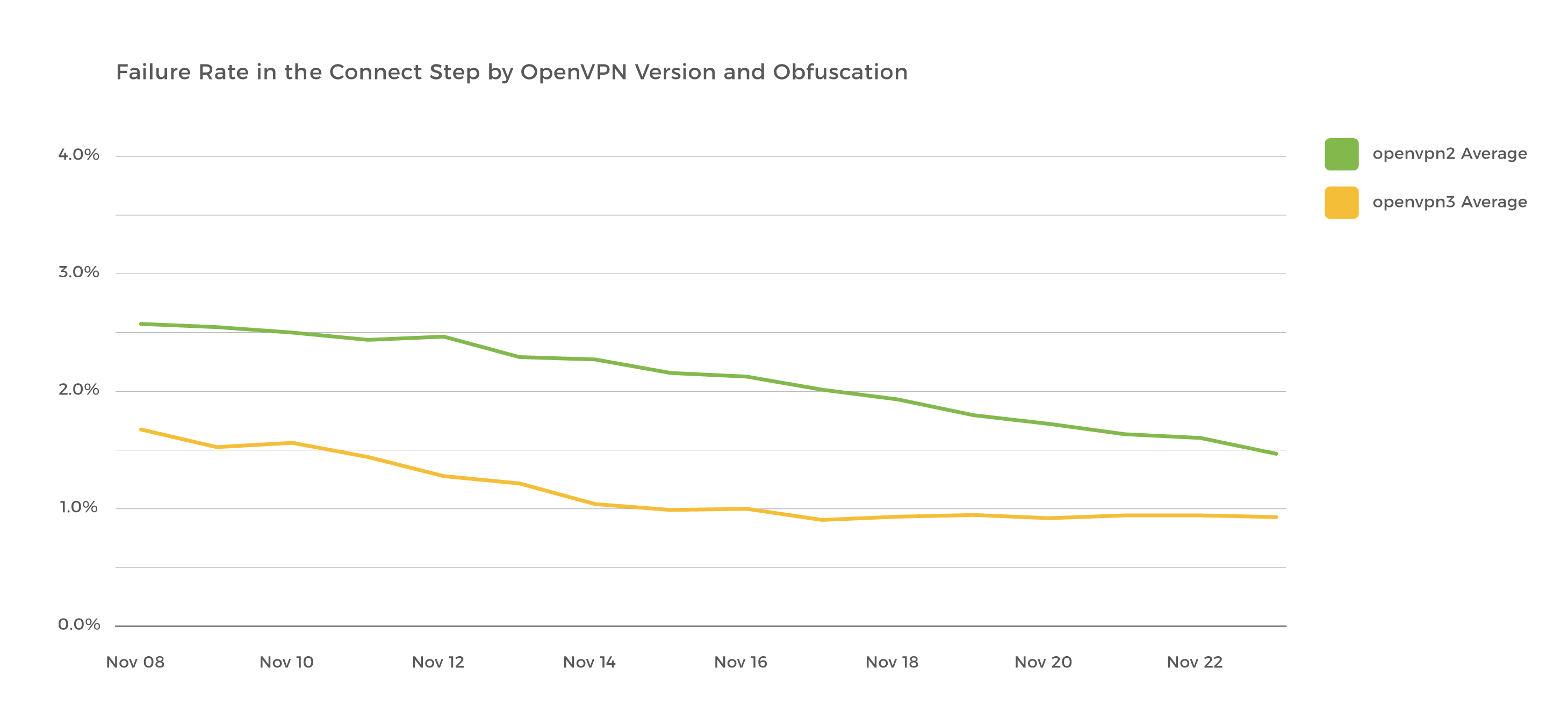
Since this implementation, we’ve seen a significant decrease in connection failures, and faster connection times. We’re also working on adding other obfuscation methods to the Android app, so if obfs4 fails we have other ways to protect you.
This is the latest step in our fight for an open and uncensored internet, but there’s more work to be done. To stay tuned on our anti-censorship work, visit TunnelBear’s internet freedom hub.
Sincerely rawrs,

TunnelBear is a very simple virtual private network (VPN) that allows users to browse the web privately and securely. It secures browsing from hackers, ISPs, and anyone that is monitoring the network. TunnelBear believes you should have access to an open and uncensored internet, wherever you are.

